Have you ever purchased an SSL certificate, and then found yourself locked into higher prices with less than optimal service? No problem! Just switch and buy from another certificate authority (or probably an intermediate CA). Well, I thought this would be no big deal. On a Linux system, generating a CSR is a simple command, but with IIS, much of this is normally hidden behind a GUI. I had the opportunity to go through this on an Exchange client access server on Windows Server 2003 R2. In my case, IIS 6.0 provides the web server for Outlook Web Access. If you try this, and you already using an existing certificate, get ready for a surprise!
To acquire a new certificate, you must generate a certificate signing request (CSR). As part of this process, a key pair is generated, and the public key is included in the CSR along with other information about your organization and the domain name(s) the certificate is supposed to validate. IIS can create the CSR through the IIS Manager. Navigate to the web site in question (perhaps the default web site), right-click and select properties. Under the ‘Directory Security’ tab, you will find a section for secure communications. Behind the ‘Server certificates…’ button you will find the capabilities for requesting and managing certificates. Now for the surprise! If you have an installed certificate, you cannot generate a new CSR!!! You can request a renewal for that certificate, but switching to a certificate from another CA is not an easy task. In short, the process is:
- Remove the existing certificate
This does not delete the certificate, but just unloads it from the server — it is still in the certificate store. - Without a certificate loaded, generate a new CSR
- Reload your current certificate
If you do not do this, your users will not be able to use the applications running over SSL. Unless you can afford a couple days of downtime while your new certificate request is validated, you have no choice but to reload the current certificate. To do this, you must delete the “pending request”, and herein lies the rub.
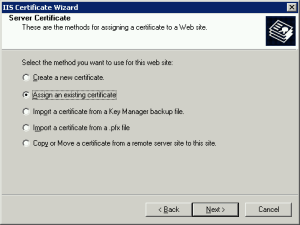
After some period of time, say 24-48 hours, your new CA determines that you (your organization) are who you say you are, and they issue you the certificate. You go back to IIS Manager, and guess what? You have no obvious method to install the new certificate! Just past the opening screen of the ‘Server certificates…’ wizard, you find this screen:
You can tell that you have a certificate installed because the ‘View Certificate…’ button is not grayed out. Your only option is:
- Remove the current certificate
But again, what’s next? When you remove the certificate, the previously pending request does not magically appear. At this point, you have one of two options. You can create a new CSR, and ask your certificate authority to re-key your certificate, or what I did:
- Attempt to install the certificate for which there is no pending request using some command-line utilities.
For this approach, follow these steps as outlined by a Microsoft TechNet article:
To install a Web server certificate that lacks a pending certificate request
| 1. | Click Start, point to Run, type cmd, and then click OK. |
| 2. | Navigate to the directory where Certutil.exe is stored; by default, this is %windir%\system32. |
| 3. | Type the following command at the command prompt: certutil -addstore my certnew.cer
where certnew.cer is the name of the certificate you received from the certification authority (CA). You should see the following message: CertUtil: -addstore command completed successfully. |
| 4. | Navigate to the directory where you stored the certificate you received from the CA. Right-click the certificate and then point to Properties. |
| 5. | Click the Details tab and select <All> in the Show drop-down list. |
| 6. | In the Field list, select Thumbprint to display its value in the view pane. |
| 7. | Select the Thumbprint value in the view pane and then click CTRL+C. |
| 8. | Return to the command prompt window and type the following command: certutil -repairstore my “thumbprint“ |
where thumbprint is the value of the Thumbprint field. Be sure to type the double quotes as part of the command. If the command is successful, the following message is displayed: “Encryption test passed CertUtil: = repairstore command completed successfully.”
| 1. | Install the server certificate on your Web server. |
![]() Important
Important
If the certutil command does not complete successfully, the following error message is displayed: “Certutil: -repairstore command FAILED: 0x80090011 (-2146893807) Certutil: Object was not found.” This message indicates that the private key for the certificate does not exist in the certificate store. You cannot install the certificate you obtained from the CA. Instead, you must generate a new certificate request, obtain the new certificate, and install that new certificate on your Web server.
Sample output is shown below:
C:\WINDOWS\system32>certutil -addstore my "myhost.example.com.crt"
Certificate "CN=myhost.example.com, OU=Information Technology, O="Example, Inc.", L=City, S=State, C=US" added to store. CertUtil: -addstore command completed successfully. C:\WINDOWS\system32>certutil -repairstore my "ce 5f 49 59 e4 eb 82 c2 18 f2 ea 51 37 59 0e e5 82 66 35 b8" ================ Certificate 0 ================ Serial Number: dfe179 Issuer: SERIALNUMBER=08759887, CN=Go Daddy Secure Certification Authority, OU=http://certificates.go daddy.com/repository, O=GoDaddy.com, Inc., L=Scottsdale, S=Arizona, C=US Subject: CN=myhost.example.com, OU=Information Technology, O=Example, Inc., L=City, S=State, C =US Non-root Certificate Cert Hash(sha1): ce 5f 49 59 e4 eb 82 c2 18 f2 ea 51 37 59 0e e5 82 66 35 b8 Key Container = 9f924c49-b2ec-4fb1-a9e3-da3cf63c2af9 Provider = Microsoft Enhanced Cryptographic Provider v1.0 Encryption test passed
CertUtil: -repairstore command completed successfully. C:\WINDOWS\system32>
And finally…
- Load the new certificate as described below.
Go back to IIS Manager, and the properties for the web site. On the ‘Directory Security’ tab, click on the ‘Server Certificate…’ button.
At this point, select the option to assign an existing certificate…
Find your new certificate in the list of certificates in the certificate store, and proceed through the wizard to the end of the process. Your new certificate is now loaded!
I haven’t looked at IIS 7.0 to know whether or not any of this has changed, but this is certainly not what you would have expected!


September 19, 2008 at 11:26
I was looking up information on how to switch CAs when I came across your site. Thanks for the information.
It looked sufficiently troublesome that I asked around and the Digicert folks said all I needed to do, if I wasn’t going to change any information about the site (CN, etc.), was to renew the cert within IIS and send the resulting CSR to the new CA who can then sign it and return it after which you’ll install it as normal.
I’m about to try it, see if it works!
September 19, 2008 at 13:03
That may very well work, but please report back to verify!!! In my case, I did in fact have some incentive to change/add information, but this is not the common case.
July 7, 2009 at 19:20
Worked wonderfully! Thanks!
Two things I did differently:
1. I double clicked on the certificate to get the certificate properties
2. Instead of removing the existing cert and then generating a request to use, I used a renewal request (with godaddy) and when I got to the step of loading the certificate, I did “Replace the current certificate” from the wizard and then selected the new cert that had been added to the certificate store.
September 11, 2009 at 20:06
This is for Windows 2003 and 2008!
It does not work on Windows 2000!
But thanks for a great walkthrough.